Secrets Management
Centrally store, access, and deploy secrets across applications, systems, and infrastructure
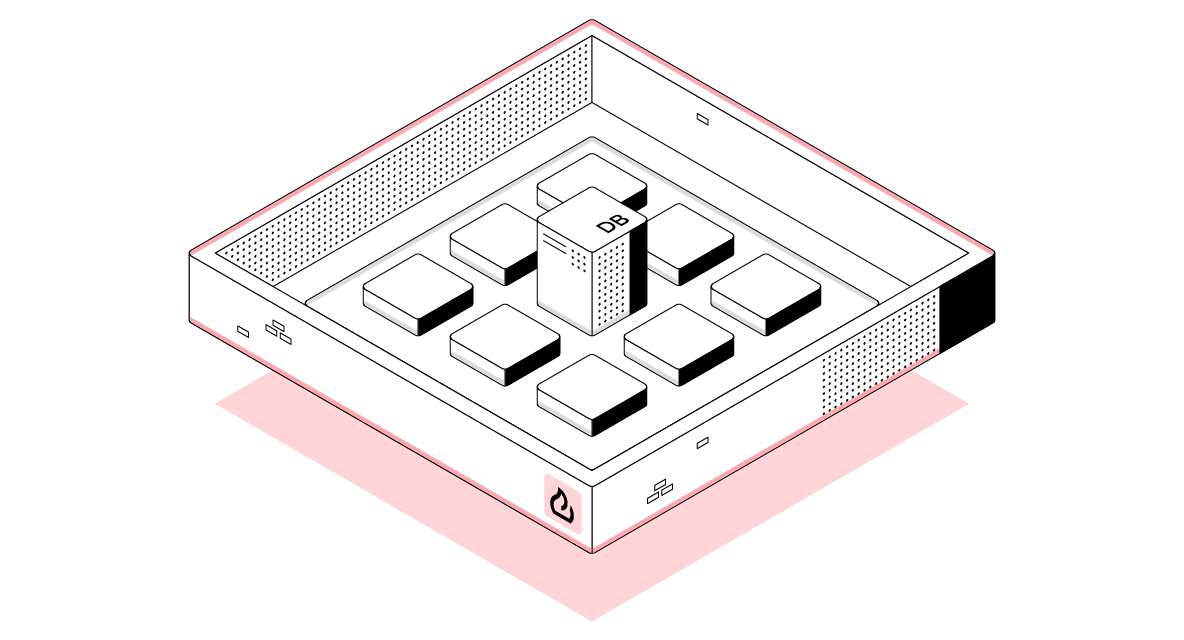
Datacenters with inherently high-trust networks with clear network perimeters.
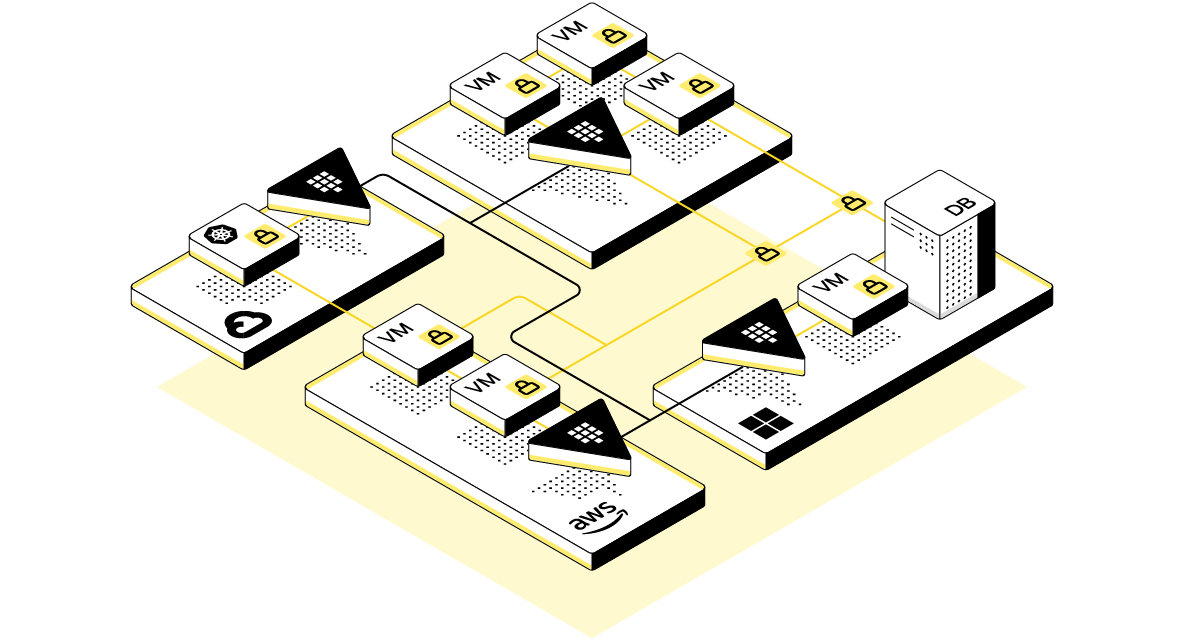
Multiple clouds and private datacenters without a clear network perimeter.



Use policy to codify, protect, and automate access to secrets.



Seamlessly integrate any trusted identity provider.
Securely manage secrets and access through a centralized workflow.