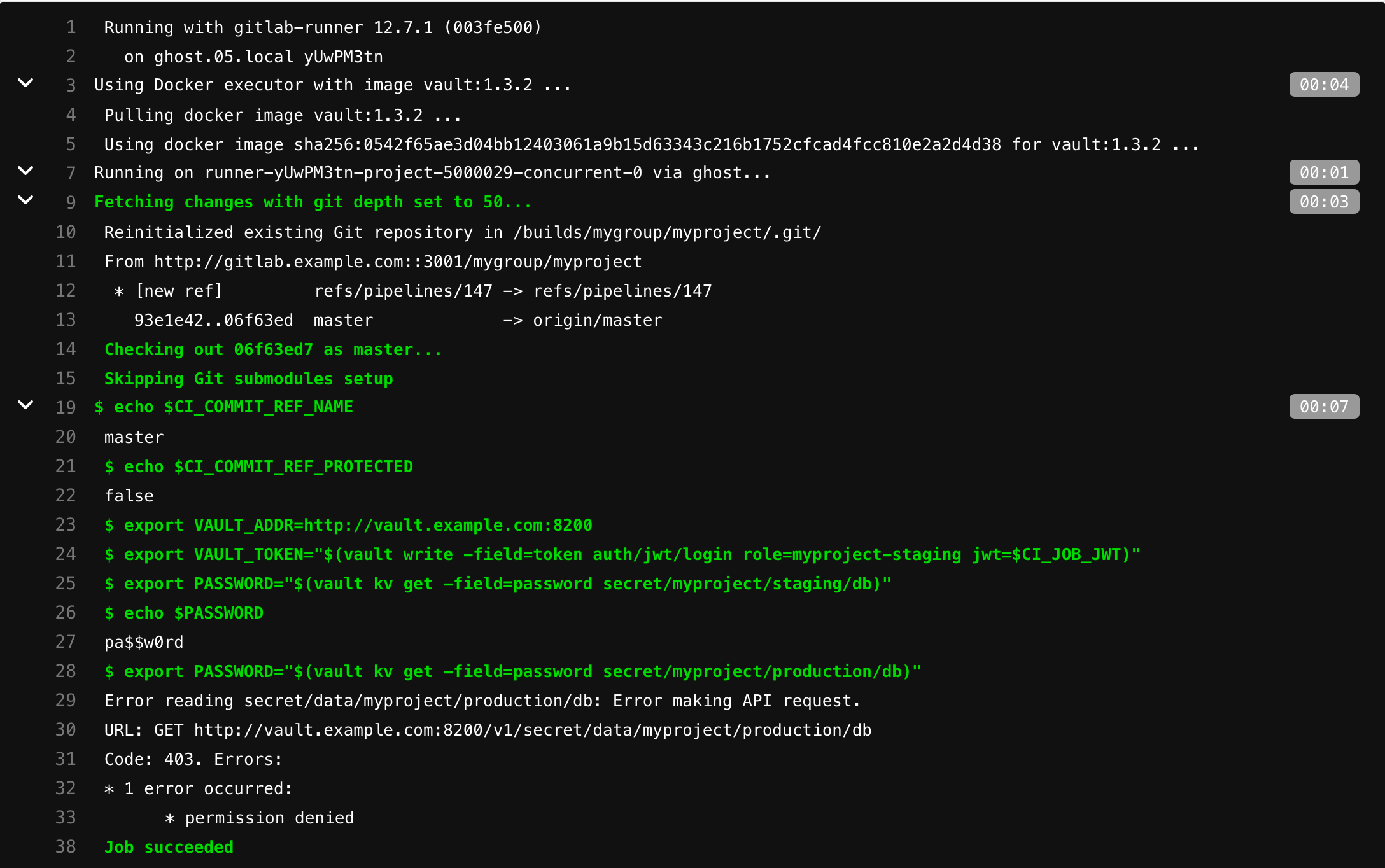
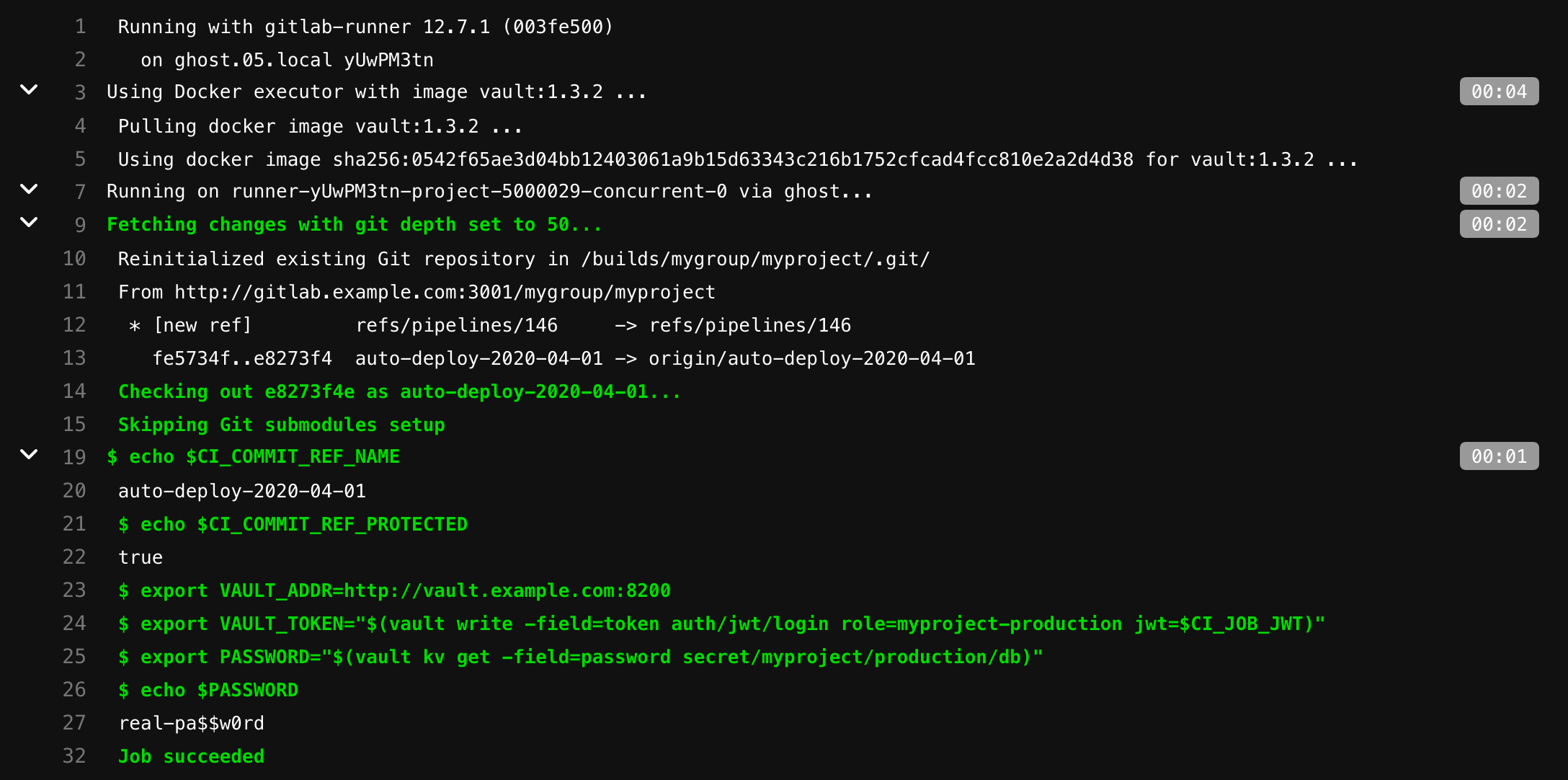
Authenticating and reading secrets with HashiCorp Vault
This tutorial demonstrates how to authenticate, configure, and read secrets with HashiCorp’s Vault from GitLab CI/CD.
use Vault secrets in a CI job.
To learn more, read Using external secrets in CI.
Requirements
This tutorial assumes you are familiar with GitLab CI/CD and Vault.
To follow along, you must have:
- An account on GitLab.
- Access to a running Vault server (at least v1.2.0) to configure authentication and to create roles and policies. For HashiCorp Vaults, this can be the Open Source or Enterprise version.
You must replace the
vault.example.com URL below with the URL of your Vault server, and gitlab.example.com with the URL of your GitLab instance.How it works
Each job has JSON Web Token (JWT) provided as CI/CD variable named CI_JOB_JWT. This JWT can be used to authenticate with Vault using the The following fields are included in the JWT: